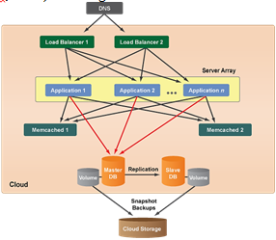
Adding a Memcached layer to cloud system architecture is essential for applications/sites that require much output from the database so as to offload a read-heavy database. This distributed memory object caching system is ideal “for speeding up dynamic web applications by alleviating database load”. See figure below:
Monthly Archives: July 2013
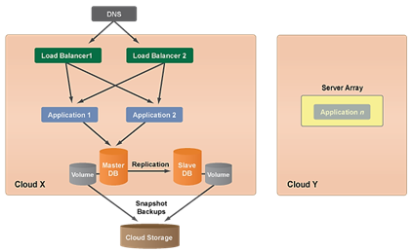
Scalable MultiCloud Architecture
The Multicloud Architecture gives application hosting flexibility in private cloud infrastructure where a Server Array for auto scaling may not be set up in a different cloud infrastructure. Furthermore, this architecture allows auto scale out into a public cloud for additional server.
Scalable MultiCloud Architecture Template
(Source: RightScale, 2012)
Scalable Architecture with Membase
Membase (Couchbase) nodes database tier is a distributed NoSQL database that can replace Master-Slave MySQL setup and suitable when attaching volumes to each node as shown below:
Template of Scalable Architecture with Membase
(Source: RightScale, 2012)
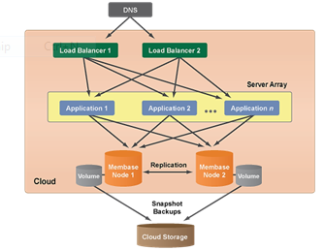
Auto scaling Architecture
With the template of the figure below Server Arrays can be used to set up a particular architecture tier to auto scale based on predefined alert conditions since a key benefits of the cloud is the ability to grow or shrink the number of running server resources (horizontally scale) as the demands of application/site change over time. This architecture is the most commonly used cloud reference architecture.
Auto scaling Architecture Template
(Source: RightScale, 2012)
Sources: Amazon and CIA ink cloud deal
According to Frank Konkel research in on a move sure to send ripples through the federal IT community, FCW has learned that the CIA has agreed to a cloud computing contract with electronic commerce giant Amazon, worth up to $600 million over 10 years.
Amazon Web Services will help the intelligence agency build a private cloud infrastructure that helps the agency keep up with emerging technologies like big data in a cost-effective manner not possible under the CIA’s previous cloud efforts, sources told FCW.
Amazon officials would not confirm the existence of the contract, and a CIA spokesperson likewise declined to comment on the matter.
“As a general rule, the CIA does not publicly disclose details of our contracts, the identities of our contractors, the contract values, or the scope of work,” a CIA spokesperson told FCW.
In recent speaking engagements, however, CIA officials have hinted at significant upcoming changes to the way the agency procures software, how it uses big-data analytics and the ways in which it incorporates commercial-sector innovation.
Speaking to the Northern Virginia Technology Council Board of Directors on March 12, Central Intelligence Agency Chief Information Officer Jeanne Tisinger told an audience of several dozen people how the CIA is leveraging the commercial sector’s innovation cycle, looking for cost efficiencies in commodity IT, and using software-as-a-service for common solutions.
Two audience members who asked not to be named told FCW that Tisinger said the CIA was working “with companies like Amazon.”
CIA Chief Technology Officer Gus Hunt would not respond to FCW’s questions about the Amazon deal, but did drop the firm’s name in relation to software procurement during a conference organized by the Armed Forces Communications & Electronics Association’s Washington, D.C. chapter in February. Hunt was quoted by Reuters as saying, “Think Amazon – that model really works,” regarding the purchasing of software services on a “metered” basis for which Amazon is well-known for. Hunt has also spoken publicly in the past about the potential for leveraging public cloud infrastructure for non-classified information.
Historically, the CIA’s cloud computing strategy centered on a number of smaller, highly specific private clouds. While the full scope of its current contract with Amazon is not yet clear, it is likely this contract essentially brings a public cloud computing environment inside the secure firewalls of the intelligence community, thereby negating concerns of classified data being hosted in any public environment.
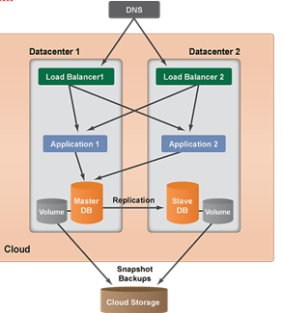
Multi-Datacenter Architecture
This architecture is suitable for cloud infrastructure that supports multiple data centers (or zones) which is often recommended to add another layer of protection and redundancy such that power failure at a particular data centers doesn’t affect the other data centers. However, data transferred between different data centers may incur additional cloud charges. See the figure below showing a template of multi-data center architecture.
Multi-Data center Architecture Template
(Source: RightScale, 2012)
Non-Redundant 3-Tier Architecture
Below shows a non-redundant 3-tier architecture template usually employed primary for basic test of the interactivity between each architecture tier and for development purposes to save on resources and costs. Since there are dedicated servers for each tier of the application/site, it is often not recommended for production environments.
Non-Redundant 3-Tier Architecture Template
(Source: RightScale, 2012)
http://support.rightscale.com/12-
Redundant 3-Tier Architecture
The figure below shows a redundant 3-tier architecture template which is essential for fail over and recovery purposes using a Server Array based application tier to take advantage of auto scaling in the cloud.
Redundant 3-Tier Architecture Template
(Source: RightScale, 2012)
webinar: Why You Should Care about Cloud Computing
In this webinar, what cloud computing means was addresses, definition of the different types, discussion on how it is impacting nonprofits and libraries, and outline some criteria for use. The challenges of using the “cloud” are discussed, as well as whether cloud computing will simplify life and reduce software and IT staffing costs.
Hear from Anna Jaeger, Co-Director, GreenTech at TechSoup Global, and Peter Campbell, Nonprofit Technologist at Earth justice. ‘Why You Should Care’ posted Oct 24, 2011
CLOUD COMPUTING PERILS
One of the huge technological trend these days is cloud computing. Many businesses are faced with the basic decision of either accepting this technology as well as transmit data versus customer’s data to “the advanced cloud” were the information could be hosted or data managed. While many companies are intrigued with the savings promised by sending their information to the cloud, money should not be a criterion for determining this decision. Cloud computing is not without risk, just like every other online endeavour cloud computing is significant
The perils of cloud computing can be critically seen when cloud computing follows the desired plan by so doing outsourcing a significant aspect of managing business information electronically. Alternatively when cloud computing goes “off the rails” the results can be very worst. For instance firstly, in 2011 one of the largest entertainment industry in the world experienced a devastating cloud computing breach. According to report of the incident, computer hackers infiltrated the cloud-computing company of which the entertainment firm had entrusted data to. 100 million customer account files were compromised because the hackers had a legitimate account set up with the cloud computing site, the cloud breach in this situation was an exceptional scenario. Secondly, the was a cloud-security breach which involved a company that delivers e-mail services to other businesses and was in charge of over 40 billion e-mails annually for more than “2,000 global brands.” After the breach in 2011, the hacked company specified that “clients’ customer data were made public by an unauthorized entry into the company’s email system. When the breach was discovered, a lot of customers of the e-mail services company sent warnings to their own customers informing them to the existence of the stolen information.